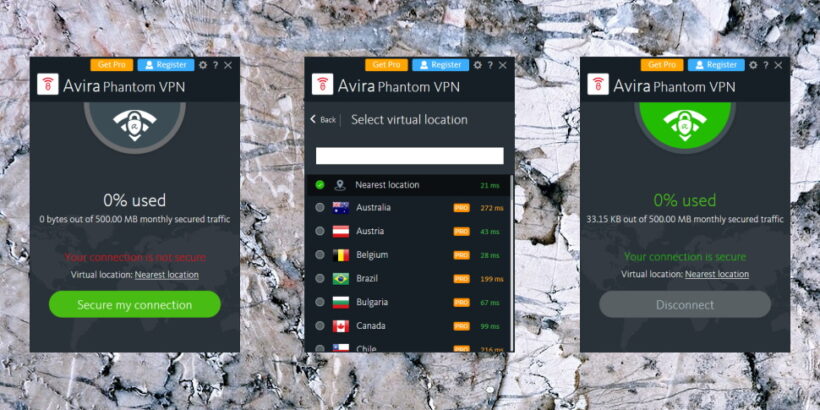
Avira Phantom VPN Crack + Product Key

Avira Phantom VPN Pro Crack Prevent exposure if your VPN connection drops by automatically blocking your internet connection. Windows only. Prevents your browser from transmitting the websites you visit your internet service provider. Ideal for streaming music shows and sports, Phantom VPN Pro unblocks access to geo-restricted services and helps you bypass college or work firewalls in any country you want to cross to access anonymously and securely your favorite websites, all in two clicks. Get unlimited access to all our products on all your devices.
Detects malware and online threats in real-time Anonymizes and encrypts your internet browsing Speeds up and cleans up your computers and cell phones Generates secure passwords you don’t have to remember with an active VPN connection, you protect your privacy, bypasses country restrictions, circumvents censorship, and cover your tracks. With the free versions of Avira Phantom VPN, you’re limited to 500MB/month of data, or 1GB/month if you sign up – but you’ll need our Unlimited VPN if you want to surf the web non-stop with Security. When you stream videos with your free account, you will run out of data very quickly.
We recommend using Avira Phantom VPN Serial Number Pro, especially when accessing public Wi-Fi networks, such as B. in hotels and restaurants. If you surf a lot online and want the best protection against cybercriminals and companies that collect data about you, Avira VPN Pro is the version of your choice. First, launch the software on your laptop or PC, or the app on your Apple or Android device. Then select the country of your virtual location and start the VPN connection. The client creates an encrypted VPN tunnel to our server and the websites you visit only see your virtual IP address. This approach brings obvious advantages.
You may also like this Hide My IP Crack
Avira Phantom VPN Crack Features
- What are the advantages of surfing the Internet with a secure VPN connection?
- You leave fewer traces All sorts of companies can track your activity as you browse the web.
- They connect as much as possible, for example, to show you personalized advertisements.
- To prevent companies from profiling you and your interests, you need to make sure that browsing the web always carries risks.
- And that connecting to a public Wi-Fi hotspot increases those risks.
- Cybercriminals hide in public places like airports, hotels, and restaurants to intercept the private data of people like you and me using these networks.
- Whenever the premium Avira Phantom VPN License Key client is active, all our incoming and outgoing data is encrypted.
- And cybercriminals have fewer opportunities to steal sensitive data such as passwords or banking information.
- Access restricted content from anywhere
- Perhaps you want to visit a country that restricts access to social networks.
- But you still want to stay in touch with your friends, or maybe you want to watch your favorite.
- TV shows while on vacation abroad.
- Many websites use location restrictions to prevent you from using their streaming service in a foreign country.
More Features
- In a DNS spoofing attack, on the other hand, the attackers manipulate the domain name service (DNS).
- To do this, they falsify the IP address belonging to a domain or a website.
- And when we visit such a manipulated website, we end up on the cybercriminals’ servers.
- without even realizing it, because the ” correct” address appears in the browser.
- Another type of man-in-the-middle attack is known in the computer world as a rogue access point.
- To bypass these restrictions, listen to your music, play your online games and watch your favorite shows wherever you are, simply launch.
- VPN Client Pro and select the country you are connecting through for unlimited access.
Avira Phantom VPN System Requirements
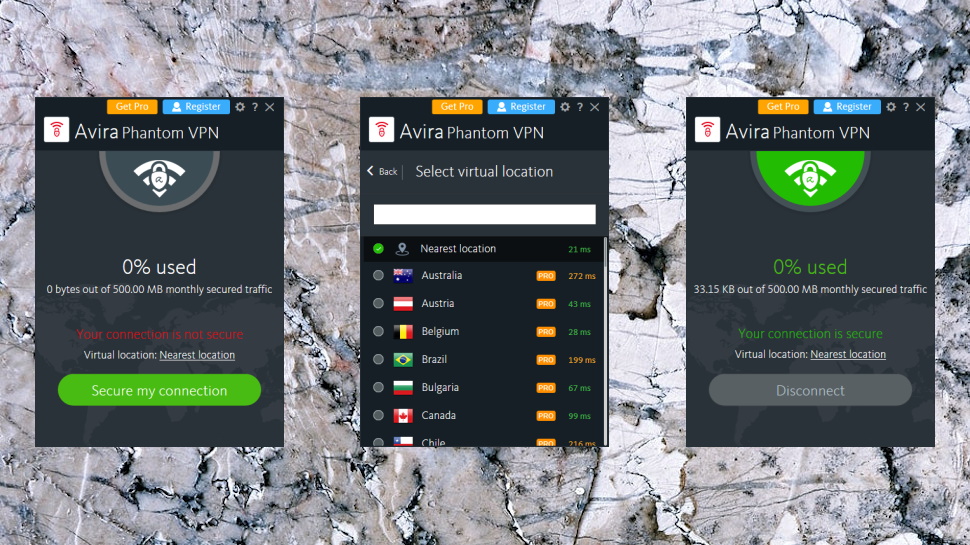
- Get unlimited data and access to 36 VPN server locations around the world.
- Your nearest virtual location is just two clicks away, so you can securely and anonymously access the content you want.
- An important additional feature of the Pro version is the kill switch.
- Which automatically blocks all data sent and received if the VPN connection is lost.
- And if you need help, just contact our technical support.
- Try out the benefits of surfing the web anonymously by downloading a free trial of our VPN client software now.
- Once you experience the benefits of enhanced features, unlimited access to 36 VPN servers worldwide, and unlimited data, you can easily upgrade to the full version of VPN Pro!:
- Contract for a monthly or annual subscription, starting once the transaction is completed.
- Click here for our terms of sale.
Setup: To start the protection/service, you need to download and install it on each device and/or complete the setup. - Free Trial Payment method required when signing up for a free trial (credit/debit card or PayPal only).
- At the end of the trial period, the paid subscription will begin and the first term will be charged unless canceled beforehand. Special offers may expire.
- Renewal Cycle Automatically renews monthly or annually after the initial term, unless subscription renewal is canceled before the date your account Avira Phantom VPN Keygen is due or by contacting us. Click here to learn how.
- Renewal Price This may be higher than the original price and subject to change.
- You will be charged up to 35 days before the annual subscription renewal and we will send you a notification email beforehand with the renewal price.
- You will be charged up to 5 days before the monthly subscription renews.
What’s New Avira Phantom VPN Crack
- Cancellation and Refund You can cancel your contract and request a full refund within 60 days of purchase for annual subscriptions and 14 days of purchase for monthly subscriptions.
- For any annual renewal or free trial with a paid annual subscription.
- you may request a full refund within 60 days of billing and, after the 60 days.
- a pro-rated refund for the remaining days of your renewed subscription period beginning in the month following your request. reimbursement.
- For the free trial with a paid monthly subscription, you can request a full refund within 14 days of billing.
- See our Cancellation and Refund Policy for more details.
- To cancel your contract or request a refund, click here.
Updates Your subscription may include product, service, and/or protection updates and features that may be added, or changed. - Removed, subject to Avira Phantom VPN Serial Key acceptance of the License and Services Agreement.
- Use For non-commercial household use only.
- If you are having trouble adding a device, please contact us.
- When sharing confidential information face-to-face, you’re probably careful not to let others hear you.
- Perhaps even whispering so no one can hear your conversation.
- Precautionary measures also apply to the virtual world, especially as we learn daily about the growing threat of cyberattacks that can strike all of us.
- We’re talking about things like man-in-the-middle attacks, where hackers manage to sneak into a confidential exchange between two parties.
How to Install it?
- Read on to learn all about what a man-in-the-middle (MITM) attack is.
- How to spot it, and how to avoid the potential consequences. What are man-in-the-middle attacks?
- Using a now-common man-in-the-middle attack, cybercriminals attempt to read, intercept, or even manipulate data traffic between two targets.
- Once they have intercepted sensitive or personal information, crooks can easily impersonate the person targeted by a man-in-the-middle attack.
- As a private person, this explanation might lead you to believe that man-in-the-middle attacks are generally less threatening since you are very careful about sharing your information.
- However, there are several common attack types that shed a different light on such a threat.
- Making you realize that Avira Phantom VPN Product Key these attacks still pose a threat.
- Different types of man-in-the-middle attacks
- ARP (or Address Resolution Protocol Spoofing) is a common type of man-in-the-middle attack.
- For example, when you visit a website, its Internet Protocol (IP) address is mapped to a Media Access Control (MAC) address before the page is even displayed.
- It is not particularly difficult for experienced cybercriminals to connect this address resolution protocol to a legitimate one.
- IP address using their own fraudulent MAC address.
- In this way, they can steal or alter data intended for the legitimate holder of the IP address.
Conclusion
Whether PC, laptop, smartphone, or tablet: all our devices automatically try to connect to the access point of the strongest Wi-Fi network in the region. Cybercriminals install their own WiFi hotspot for this type of man-in-the-middle attack. This means that if you’re near that naturally unsecured Wi-Fi network, your device might automatically connect to it. This then gives the attacker free access to everything you send and receive, allowing them to manipulate the traffic as they see fit. Cybercriminals use many variations of kidnapping or hijacking methods.
Before we dive deeper into some of these methods, here are a few examples: In the case of a browser hijacker, for example, malware that you end up installing without your knowledge alters your browser settings. This malware runs in the background and can wreak Avira Phantom VPN Pro Activation Key havoc, including changing your homepage or redirecting your search queries to malicious websites. In domain hijacking, hackers – illegally of course – hijack the domain from the rightful owner and impersonate the owner, which is a pretty aggressive form of hacking. Content hijacking occurs when other website content is loaded in addition to the actual website content.