Avast Driver Updater Crack + Product Key
Avast Driver Updater Crack software for free to easily scan, update and repair your PC’s drivers – no credit card required. Driver Updater detects old, corrupt, missing, or outdated drivers, fixes errors and vulnerabilities, and backs up and restores current drivers. Drivers are programs, and sometimes programs can be buggy or contain security vulnerabilities. These vulnerabilities can be exploited by attackers to gain access to your data or make changes to your operating system. Driver Updater scans for vulnerabilities, identifies outdated or faulty drivers, and notifies users when a security update is available. Easily improve your PC’s performance.
Driver Updater finds the latest driver versions for maximum stability with fewer errors, connection issues, and mouse or printer issues. Update graphics drivers to improve performance and enjoy crisp images in games, virtual reality, multimedia applications, streaming, and media editing. Is no sound coming out of your speakers? Does Wi-Fi keep dropping? Has the printer suddenly stopped working? Driver Updater eliminates these interruptions. Avast has added the wizard to Driver Updater. The wizard guides users along the way to restore specific drivers based on the type of issues users are having and when the problem occurred.
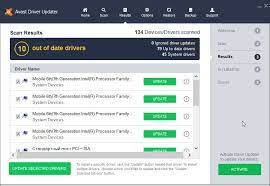
After completing the process with the wizard, the accessory should work properly again. Our one-click scan makes it easy to find the drivers you need for your printer, scanner, camera, speaker, keyboard, router, and other devices. Automatically scans your computer for corrupt, missing, and outdated drivers
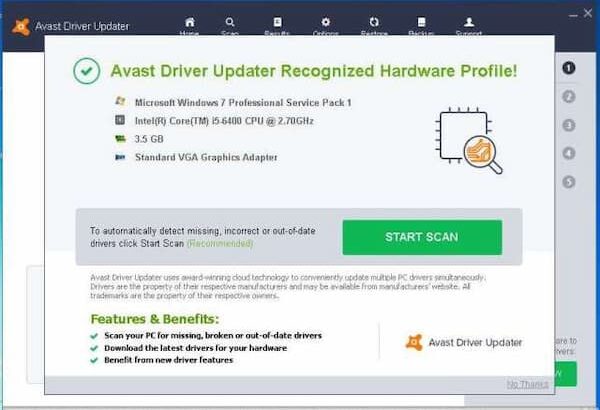
Avast Threat Labs checks security to make sure every driver is safe and secure before it reaches your PC Checks over 300,000 hardware devices Checks for the latest updates in real-time
Creates and manages your unique PC profile for quick access to the drivers you need to keep your computer.
You may also like this Removewat Crack
Avast Driver Updater Crack Features
- Backs up your drivers to undo unwanted changes
- Prevents hardware issues with a scaled installation process.
- After all, human curiosity is what attackers exploit.
- However, plugging an unauthenticated device into your own or work computer can be very dangerous.
- And USB drives are still a common way for attackers to infect computers with viruses and malware.
- They can damage your devices and data in seconds.
- If you think this can’t happen to you, think again!
- You can find a malicious USB Avast Driver Updater License Number on the street, at school, or at work.
- The USB security problem is more complex than ever, and the popularity of associated threats has only been fueled by.
- The growing presence of online video tutorials on how to make these devices and the growing availability of hardware.
- We’re not just talking about USB drives – other USB devices can also be infected, including seemingly harmless cables.
- Besides the case of “lost” USB drives mentioned above, there are also cases of malicious USB drives that people receive for free as promotional material at conferences, job fairs, or other events.
- Briefly, malicious USB attacks can be divided into the following steps:
- First, the attacker uploads malicious code to the USB device which runs when plugged into a computer or when the user displays an infected file stored on the drive opens.
- If the user has an antivirus program installed on their device, the risk is greatly reduced – because an antivirus program can detect malicious behavior and stop the attack.
- The second option is to configure the hardware of the USB device so that the computer perceives it as a keyboard or webcam when connected.
More Features
- This makes it easier for an attacker to breach security measures and infect the user’s computer with malware.
- The most common type of these malicious devices is the so-called.
- Rubber Ducky, which looks like an ordinary USB key but actually imitates a keyboard.
- When connected to a computer, it can “press” specified keys and execute malicious code.
- Rubber duck appears.
- A malicious USB device Avast Driver Updater License Key can allow a victim to steal saved passwords, access confidential files, or directly open a backdoor to take control of a device.
- In rare cases, the device may even be so damaged that it can no longer be used.
- Malicious USB drives can also be an effective way for cybercriminals to circumvent certain corporate security measures.
- You can use them to access an organization’s computer, server, or network.
- An attacker usually only has to wait for an employee to voluntarily connect the device to their work computer.
- Beware of unauthenticated devices: Only connect personal USB devices to your computer so that you know what they contain and what they are used for.
- Don’t connect a drive that you found somewhere or don’t know who owns it to your computer.
- Automatically disconnect USB devices: You can control which devices can automatically connect to your computer in your computer settings.
- We recommend disabling this option for all devices.
- This gives you more control over your computer and prevents connected USB devices from automatically running programs.
Avast Driver Updater Crack System Requirements
- Use antivirus: You can prevent some attacks from a malicious USB drive if you protect your computer with a robust antivirus.
- Cryptocurrencies have been around for over a decade now. Since their inception, they have grown in importance as a legitimate form of currency.
- However, with the growing popularity of cryptocurrencies, the use of cryptocurrencies for cybercrime has also increased.
- Why is that? Throughout the history of cybercrime, there have always been money management issues.
- Since cybercriminals can be anywhere in the world, far from their victims, it makes no sense for them to work with physical currency.
- The use of traditional banking services has also been banned, as law enforcement can follow the leads of bad actors and use them to arrest them.
- To get around this problem, they used Western Union or online services.
- Webmoney or E-Gold, which all had one thing in common: they didn’t need a bank Avast Driver Updater Keygen account or credit card.
- When cryptocurrencies were created, they were quickly recognized as an ideal vehicle for cybercriminals to launch malicious attacks.
- The acceptance of cryptocurrencies in the cyberattack landscape has been rapid, and there’s a good reason for that: the anonymity they offer.
- Transactions made with cryptocurrencies do not require any personal information and because of this, it can be difficult to trace the people behind them.
- Another major reason why cybercriminals are attracted to cryptocurrencies is their decentralized nature.
- Unlike traditional currencies which are controlled by governments and financial institutions, cryptocurrencies operate on a decentralized system.
- This means that transactions are recorded on a public ledger, also known as the blockchain, which is not controlled by a central authority.
New Update
- This, in turn, also makes it much harder for law enforcement to track transactions and determine the identities of those involved in crypto-related cybercrime.
- Cybercriminals have found many ways to use cryptocurrencies to their advantage.
- One of the most common means is ransomware attacks.
- In a ransomware attack, a cybercriminal gains access to a victim’s computer and encrypts their files, making them inaccessible.
- The cybercriminal then demands a ransom in the form of cryptocurrency (usually Bitcoin) in exchange for the decryption key.
- Which will allow the victim to regain access to their files.
- The most popular cryptocurrencies used by cybercriminals are Bitcoin, Monero, and Ethereum.
- Bitcoin: As the first and most well-known cryptocurrency, Bitcoin remains the most Avast Driver Updater Serial Key popular choice among cybercriminals as it has the highest liquidity and is the most widely used payment method on the dark web.
- Although bitcoin transactions are recorded on the blockchain, allowing law enforcement to track transactions.
- It is still much more difficult than tracking traditional forms of currency.
- Monero: Due to its built-in privacy features, Monero is another popular choice among cybercriminals.
- Monero transactions are designed to be private and untraceable, making it much harder for law enforcement to trace transactions.
- Additionally, Monero uses a technique called “ring signatures” which makes it difficult to determine the identity of the person behind a transaction.
- Ethereum: Like Monero, Ethereum is another cryptocurrency that offers some degree of privacy and untraceability.
- It is another popular choice among cybercriminals.
What’s New Avast Driver Updater Crack
- The three examples above each show that cybercriminals tend to prefer cryptocurrencies that offer some level of anonymity and untraceability.
- Cryptocurrency-based scams are another way cybercriminals exploit the use of cryptocurrencies.
- Many of these scams are Ponzi schemes, in which an individual or a group of individuals promise high returns with little or no risk. In reality.
- The scammer will ask for the Avast Driver Updater Product Key an initial investment in the form of cryptocurrency and then use the money from the new investors to pay back the previous investors.
- This creates the illusion of a profitable investment, but eventually, the system breaks down, leaving investors with nothing. Initial coin offering (ICO) scams are also increasingly common.
- In these scams, a company or individual creates a new cryptocurrency and offers it for sale to the public.
- They will make false claims about the potential of cryptocurrency and then walk away with all the money they have raised.
- Cybercriminals also exploit the use of cryptocurrencies through phishing scams.
- where they trick victims into revealing their personal information such as private keys or sending money to a fake wallet address.
- And of course, we can’t stop at the different forms of cryptocurrency-related malware.
- Trojans steal wallets to threats that secretly install miners on computers and smartphones.
- Or any other device in order to harness the computing power of victims to mine their favorite cryptocurrency.
How to Install it?
- With this in mind, it is clear that a strong link has been established between cryptocurrencies and cybercrime.
- Cybercriminals are attracted to the decentralized nature and anonymity of cryptocurrencies.
- Which makes it difficult for law enforcement to track them down.
- It is important for individuals and businesses to be aware of the potential risks associated with cryptocurrencies and take steps to protect themselves.
- Including Being vigilant about unsolicited requests for personal information or money.
- Beware of investment opportunities that sound too good to be true.
- The dark web remains a small, Avast Driver updater Activation Key hidden part of the internet with strong ties to illegal activities and should be approached with caution.
- When it comes to the internet, most of us are only scratching the surface.
- The vast majority of what we know and use on a daily basis is the “surface web”.
- Which encompasses all websites easily accessible through a search engine like Google or Bing.
- But beyond the Surface Web lies a much larger and more mysterious realm known as the Deep Web.
- And within this Deep Web lies an even more mysterious and controversial corner of the Internet known as the Dark Web.
- So what exactly is the dark web?
- To understand this, it helps to first understand the difference between the surface web and the deep web.
- The Surface Web is the part of the Internet that is easily accessible to the public.
- It’s the part of the internet that we all know and uses on a daily basis.
Conclusion
The deep web, on the other hand, is the part of the Internet that is not indexed by search engines. The Deep Web isn’t necessarily bad, but it’s also not easily accessible to the public. The dark web is a whole different beast. It is a small part of the deep web that is intentionally hidden and only accessible through special software like the Tor browser. Often associated with illegal activities, the dark web Avast Driver Updater Crack has earned a reputation as the digital wild west. The dark web is a collection of websites and services that exist on an encrypted network and can only be accessed through special software such as the Tor browser. These websites and services are often anonymous and operate outside the jurisdiction of law enforcement and government surveillance.
The dark web is often associated with illegal activities such as drug trafficking, illegal gun sales, and hacking services. However, not all activity on the dark web is illegal. For example, journalists and activists have used the dark web to communicate and share information without fear of government surveillance. Additionally, some people use the dark web to anonymously purchase legitimate goods and services. It is also important to understand that the dark web is not synonymous with the deep web. As mentioned above, the deep web includes any part of the internet that isn’t indexed by search engines, and that’s not necessarily bad.